Implementing App Isolation in vRA 8 Cloud Assembly Blueprint
I will start by saying that as of today (12/12/2019), this process is not yet documented, however it is working as expected.
Using vRealize Automation 7.x, you might have used App Isolation checkbox in the blueprint settings screen in-order to have a bubble environment (Documentation Link) with outbound connection to corporate network, with you could add DFW rules in NSX to specific destination. In vRealize Automation 8.0 it is gone.
In vRealize Automation 8.0 , this can be implemented several methods, including some Orchestrator code, but the most straight-forward way is to implement a network profile that creates an on-demand security group for each deployment, and set the network connection in blueprint to outbound; using this kind of configuration, vRA will create a DFW section with isolation rules and add VMs to the security group.
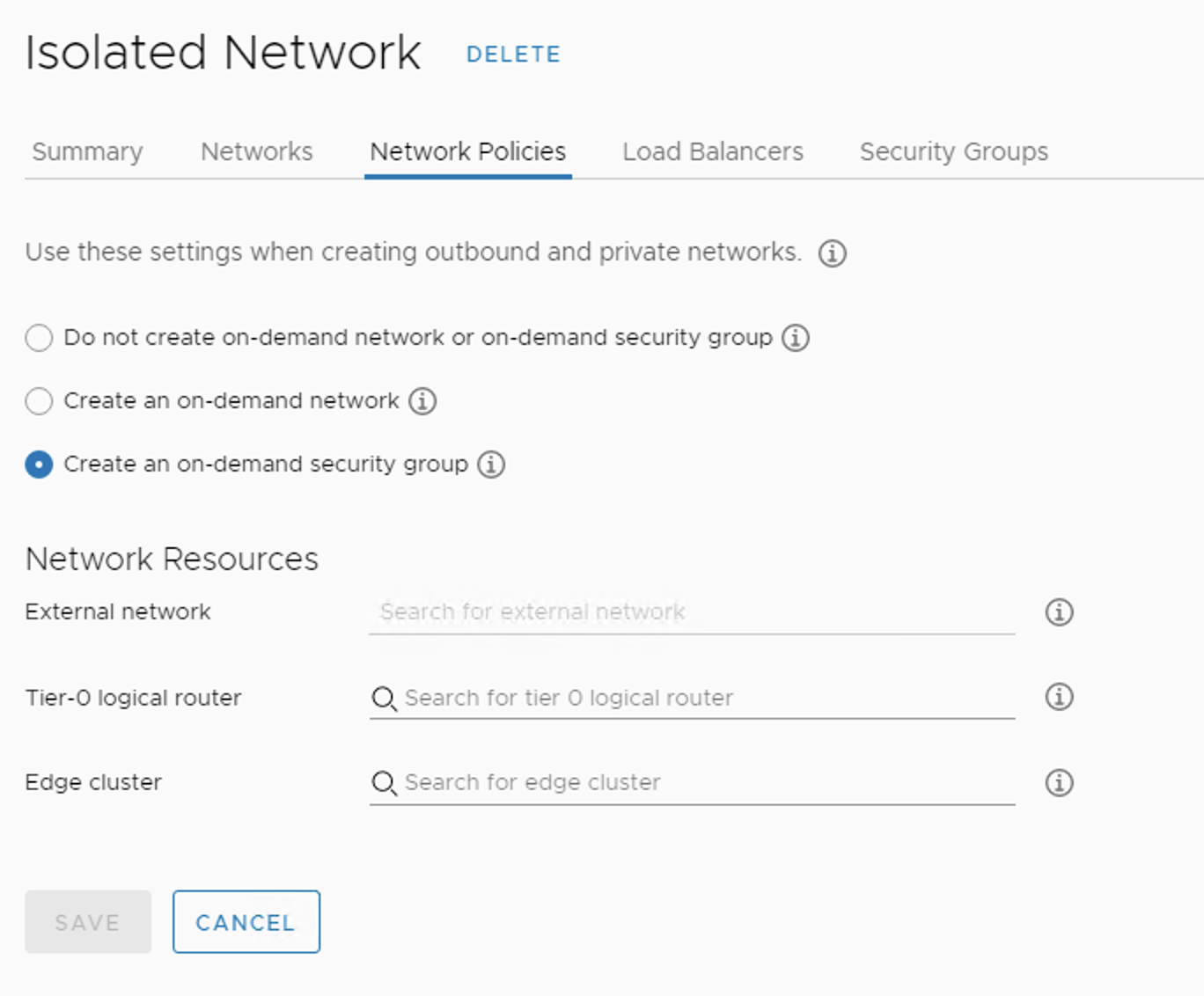
In The network profile, under Network Policies, check “Create an on-demand security group“, similar to the below image.
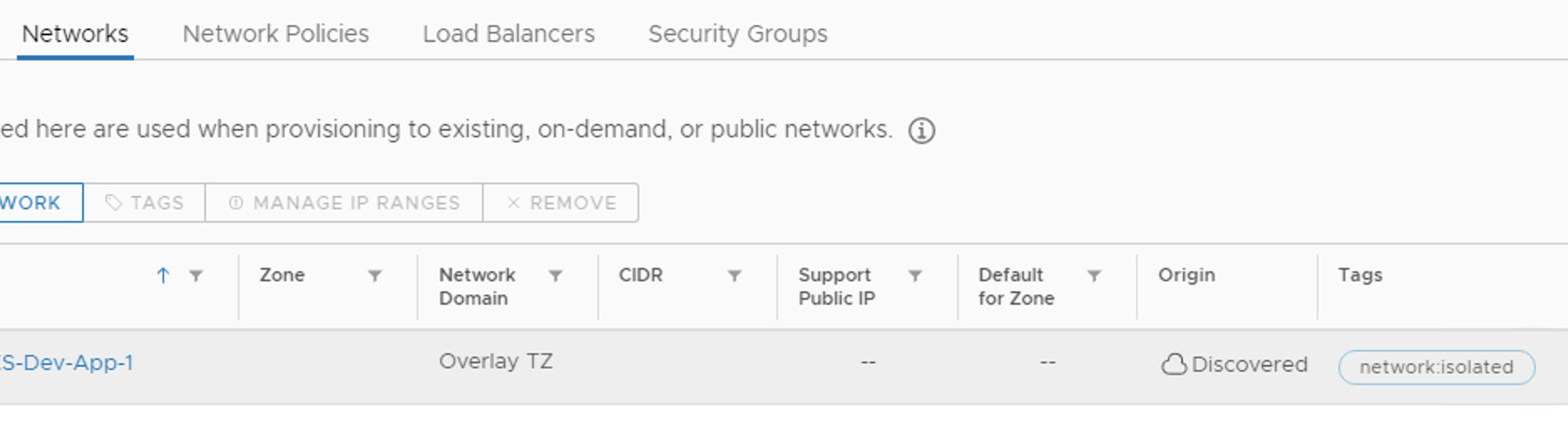
The Blueprint need to specify network with type: “outbound“, in my example I am using tag based constraints where the Logical Switch was tagged with “network:isolated“.
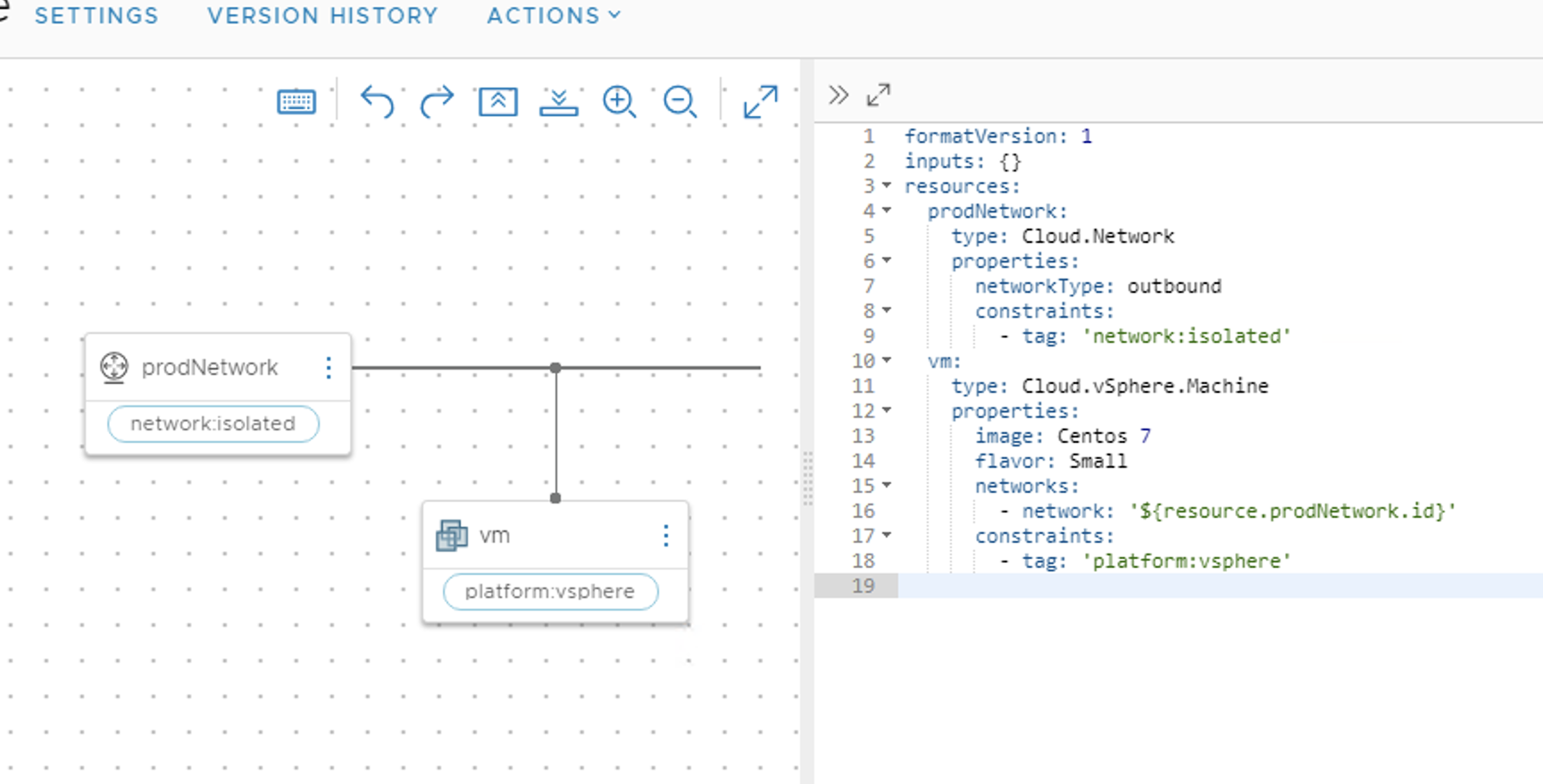
result would be a new DFW section, isloation nsgroup with member Logical Ports, and accommodating firewall rules, as so
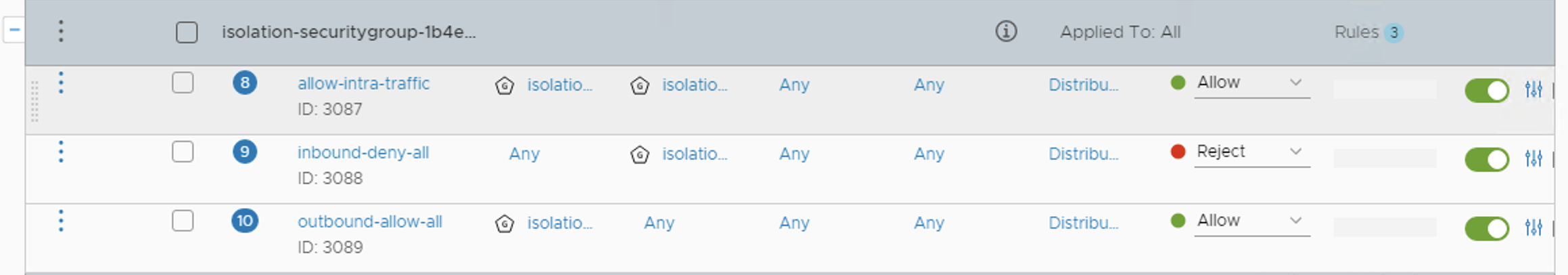
Here is the example blueprint for download.